Single sign-on (SSO) configuration
Single sign-on (SSO) configuration is an admin-only feature on upgraded accounts and you can only see the “Security” tab in organizations where you are an organization admin.
To avoid unauthorized logins, we have introduced an organizational-level security setting “Configure SSO” to mandate employees to log in via SSO. This “Configure SSO” setting will allow configuration at a domain level so an SSO type can be configured independently for each domain. Once SSO is configured for a domain, all employees associated with that particular email domain will:
-
be blocked from using a username/password to log into Podio
-
need to mandatorily use only the configured SSO type to log into Podio on both web and mobile.
Configuration
-
SSO Configuration can be done from the “Security” tab available alongside the Organization settings.**
The “Security” tab is available only to organization admins for a paid organization and to all employee users for free organizations.
-
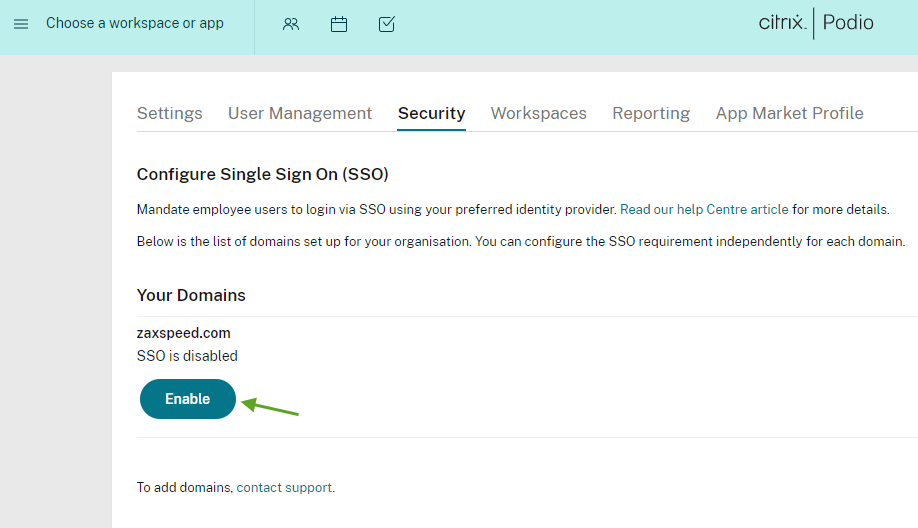
Setting up a domain is a prerequisite for being able to configure SSO for the organization. If you do not have a domain added to your organization, please contact Support to add the domain(s).**
Each domain needs to be configured with the SSO type that matches the identity provider configured for users on the domain. Example: One organization could have different domains across GEO locations which might be following different SSO requirements.
-
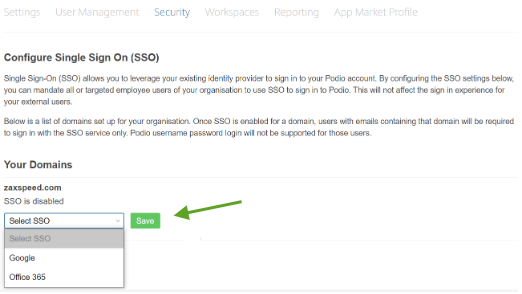
Currently SSO Configuration is allowed for only 2 identity providers (IdP) that Podio already supports:**
-
Google (G Suite or Workspace)
-
Microsoft (Office 365)
Pro Tip:
This could allow you to utilize an alternate IdP indirectly. For example, if your organization supports Okta SSO and you sign in to O365 using Okta, you will eventually be able to login to Podio using Okta via O365. For this, you will need to Configure SSO with Office 365.
-
Note:
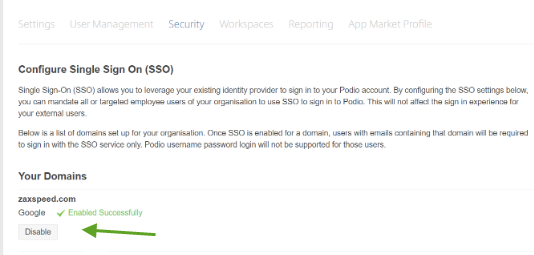
Single sign-on (SSO) can be disabled from the Organization Security page by simply clicking the “Disable” button.
User login flow
Step 1: SSO check of email being used to login
- A user enters email with domain @abc.com for username password login.
- System will check if there are any SSO settings for domain @abc.com.
- If SSO setting found, the username password login will be denied
- If no setting found, then Step 2
Step 2: SSO check of all associated emails
- System will check if the user has any other email associated with this user id.
- If no other email found, then user will be allowed to login successfully with username password
- If associated email(s) are found, let’s say, the other emails associated have domain @xyz.com and @def.com respectively. Now system will check if there are any SSO settings for either of these domain @xyz.com and @def.com
*If SSO setting found for any of the domains, the username password login will be denied
- If no setting found for either of the domains, then user will be allowed to login successfully with username password
If SSO has been enabled for at least one or more emails associated with the user, then for every case of denied login, an email notification will be sent out to the appropriate email ids associated with the configured SSO.
Advanced Information and FAQs
Q: Are all members inside of my Podio organization required to use SSO login once this feature has been enabled?
A: Only employee members inside of your Podio organization will be required to use SSO login once this feature has been enabled. This feature will not be applicable to external members within your Podio organization.
Q: Even though my organization uses SSO login, would I still be required to use SSO login if my account is also a member of organizations that don’t have this feature enabled?
A: Yes, you’ll still be required to use the mandated SSO login linked to one of the organizations that have this feature enabled as Podio will give SSO priority to the higher security constraints.
Q: Can I login to Podio using one of my non Single sign-on (SSO) alternate account email addresses even though I’m an employee member of Single sign-on (SSO) Podio organization?
A: No, if you’re an employee member of an organization that has single-sign-on (SSO) enabled, you’ll receive an error while attempting to login using the non single-sign-on (SSO) alternate email address.
Error: ”Sorry, single-sign-on (SSO) has been enabled by one of your organizations. Please sign-in using the appropriate SSO provider.”
Q. The Google SSO isn’t working for me as I have Advanced Protection features on my Google Workspace Enterprise account. How to solve this?
A: To fix this, your Google workspace admins will have to add Podio as a trusted third-party app from the Google marketplace.