This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Automated Threat Remediation
Understanding Automated Threat Remediation: Enhancing Security with Proactive Measures
As cyber threats evolve in complexity and volume, traditional reactive security measures are no longer sufficient. This is where automated threat remediation comes into play, a forward-thinking approach that addresses and neutralizes high-severity threats in real-time, safeguarding both user data and platform integrity.
What is Automated Threat Remediation?
Automated Threat Remediation refers to the automated process of identifying and resolving security threats without human intervention. By leveraging advanced machine learning models, our system can detect anomalies that indicate potential security risks. Once a threat is identified, the system proactively takes predetermined actions to mitigate the risk, ensuring the security of our platform and its users.
Why does ShareFile offer Automated Threat Remediation?
The landscape of cyber threats is constantly changing, with attackers finding new ways to exploit vulnerabilities. Auto remediation offers a dynamic defense mechanism that adapts to emerging threats, providing continuous protection. It reduces the time from threat detection to resolution, minimizing potential damage. Moreover, it alleviates the burden on our security teams, allowing them to focus on enhancing our defenses rather than responding to incidents after they occur.
Actions taken on different scenarios
Our automated threat remediation system employs a range of measures designed to protect user data and platform integrity in response to various security threats. Instead of detailing specific actions, which might cause concern, we emphasize our commitment to maintaining a secure environment for all users. Here’s an overview of our approach:
-
Proactive Measures - We continuously monitor for signs of unusual activity, employing advanced algorithms to detect and address potential threats before they can impact our users or platform.
-
Customized Security Protocols - Depending on the nature and severity of the threat detected, our system implements tailored security protocols. These are designed to effectively neutralize threats while minimizing any inconvenience to our users.
-
Continuous Protection - Our security measures are always active, providing constant safeguarding against a wide array of cyber threats. This ensures that our users can trust in the security of their data and our platform at all times.
-
User Empowerment - While we handle the technical side of threat mitigation, we also provide our users with guidance and tools to enhance their own security. This collaborative approach strengthens overall protection and empowers users to maintain secure accounts.
Here are examples of how we address two common scenarios:
-
Scenario 1 - Login Attempts from Multiple Countries: When our system detects login attempts from a wide range of geographic locations in a short timeframe, it recognizes this as unusual activity that could indicate a security risk. In such cases, we implement protocols designed to verify the legitimacy of these attempts and safeguard the account, all while ensuring minimal disruption to the user.
-
Scenario 2 - Downloads from Many Countries in a Specific Duration: Similarly, if our system observes downloads originating from multiple countries within a brief period, it triggers our automated threat remediation measures. These actions are calibrated to assess and address the potential threat, ensuring that any unusual download patterns do not compromise account security or data integrity.
Notification Process
Whenever an action is taken, we ensure that all affected parties are promptly informed:
-
Account Owner Notification The account’s owner is notified through email about the threat and the action taken, providing an overview of the security incident.
-
User Notification Along with the Account Owner the actual user whose account is involved in the incident receives an email notification detailing the threat and the necessary steps to restore account security.
Frequently asked questions
What happens if there’s a login from multiple countries to my account?
I received an email saying there was a login attempt from several countries to my account. What does this mean?
This notification means our system detected login attempts to your account from multiple geographic locations within a short period. This activity is often a sign of unauthorized access attempts by cybercriminals who might have obtained your credentials through phishing or other means.
What actions are taken when such activity is detected?
For your protection, we immediately mandate a password reset. This means you will not be able to log in to your account until you create a new password. This measure is crucial to prevent further unauthorized access.
Who gets notified when there’s a login from many countries?
An email notification is sent to you, the account holder, to inform you of the potential compromise. Additionally, the Account Owner of your organization is also notified. This ensures that all concerned parties are aware and can take necessary steps to secure your account and the system.
What if there’s unusual download activity from my account?
What constitutes unusual download activity, and how do you respond to it?
Unusual download activity is when our system notices downloads from your account across different countries within a specific duration that doesn’t align with normal usage patterns. This could indicate someone else is accessing your account.
What immediate actions are taken to secure my account?
Similar to the first scenario, we mandate a password reset for your account. You will not be able to access your account until you set a new password. This step is vital in safeguarding your information from further unauthorized access.
How am I notified about the unusual download activity?
An email notification is dispatched to you and the Account Owner, detailing the unusual activity and the steps we’ve taken to protect your account. This communication is essential for transparency and to prompt any additional actions you may need to take.
Threat detection & remediation visibility
What is Remediation visibility
Remediation Visibility is a feature that provides users with detailed insights into Autoremediated security alerts. It provides clarity by displaying specific information related to the alert, such as the geographic locations involved in impossible travel scenarios, the number of IPs and access dates for alerts related to accessing from multiple IPs, and the number and timing of downloads for high download alerts. This visibility helps users better understand and respond to potential security threats.
What feature does Remediation Visibility provide?
To enhance user understanding of security alerts, Remediation Visibility has been introduced. This feature provides detailed insights into specific alerts, allowing users to take informed actions.
-
Impossible Travel Scenario: Users can view the number of countries involved including the location of countries from where they have access displayed on map.
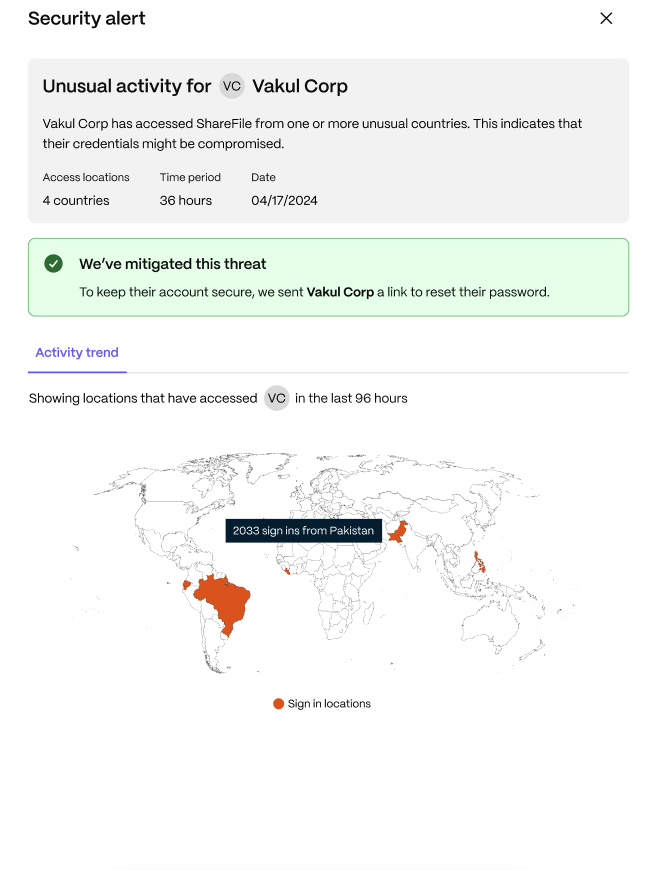
-
Trend Change - Accessing from Multiple IPs: Users can see multiple IP addresses signed-in, and view an activity trend that shows the specific number of IP was accessed on specific dates.
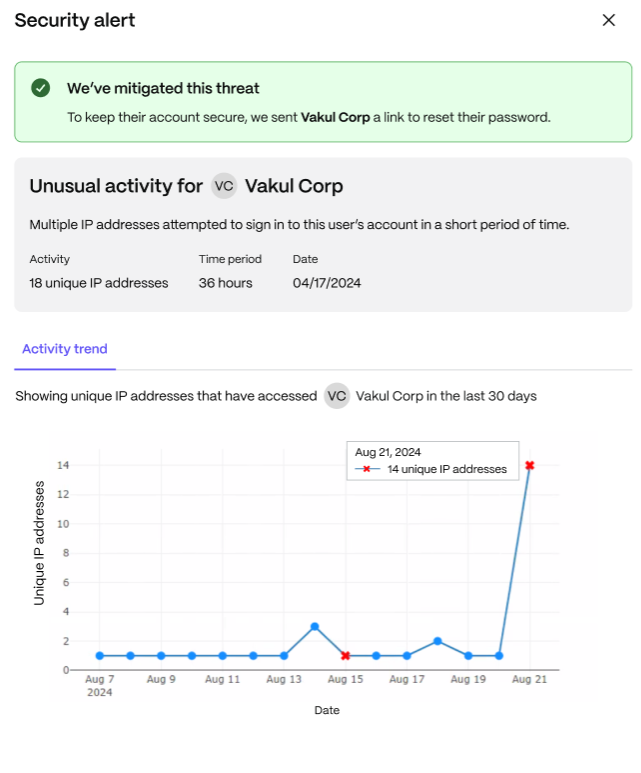
-
Trend Change - High Downloads: Users can see the total number of downloads and use the activity trend to monitor the number of downloads on specific dates.
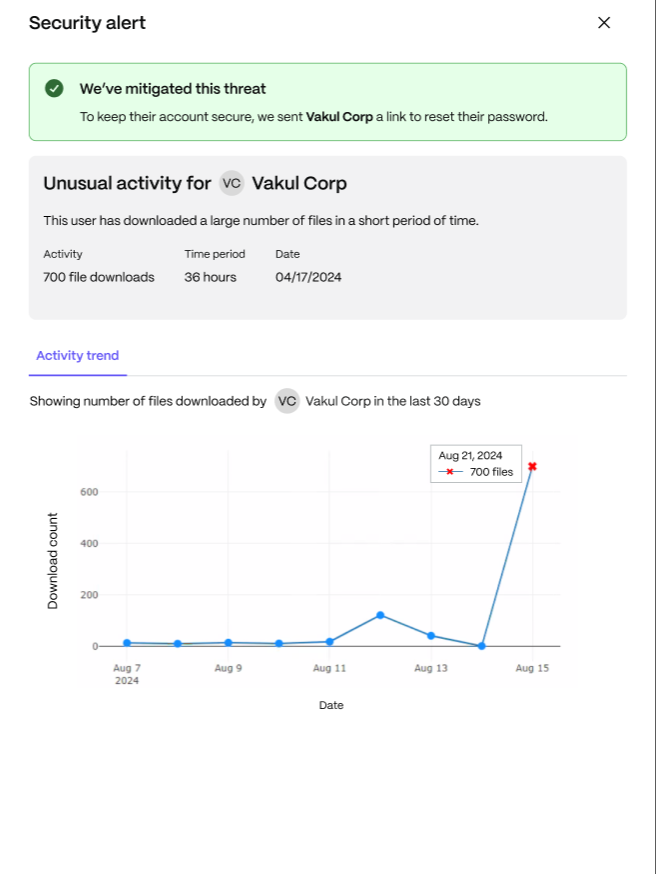
Remediation Visibility offers a clearer and more detailed view of these alerts, empowering users to understand and respond to potential security threats more effectively.
Opt-out from Automated Threat Remediation
The “Opt-out from Automated Threat Remediation” feature allows account administrators to disable specific automated threat remediation scenarios within their security settings. This means administrators can customize the security measures to better fit their organization’s needs and preferences. Only account administrators have the authority to access and use this feature.
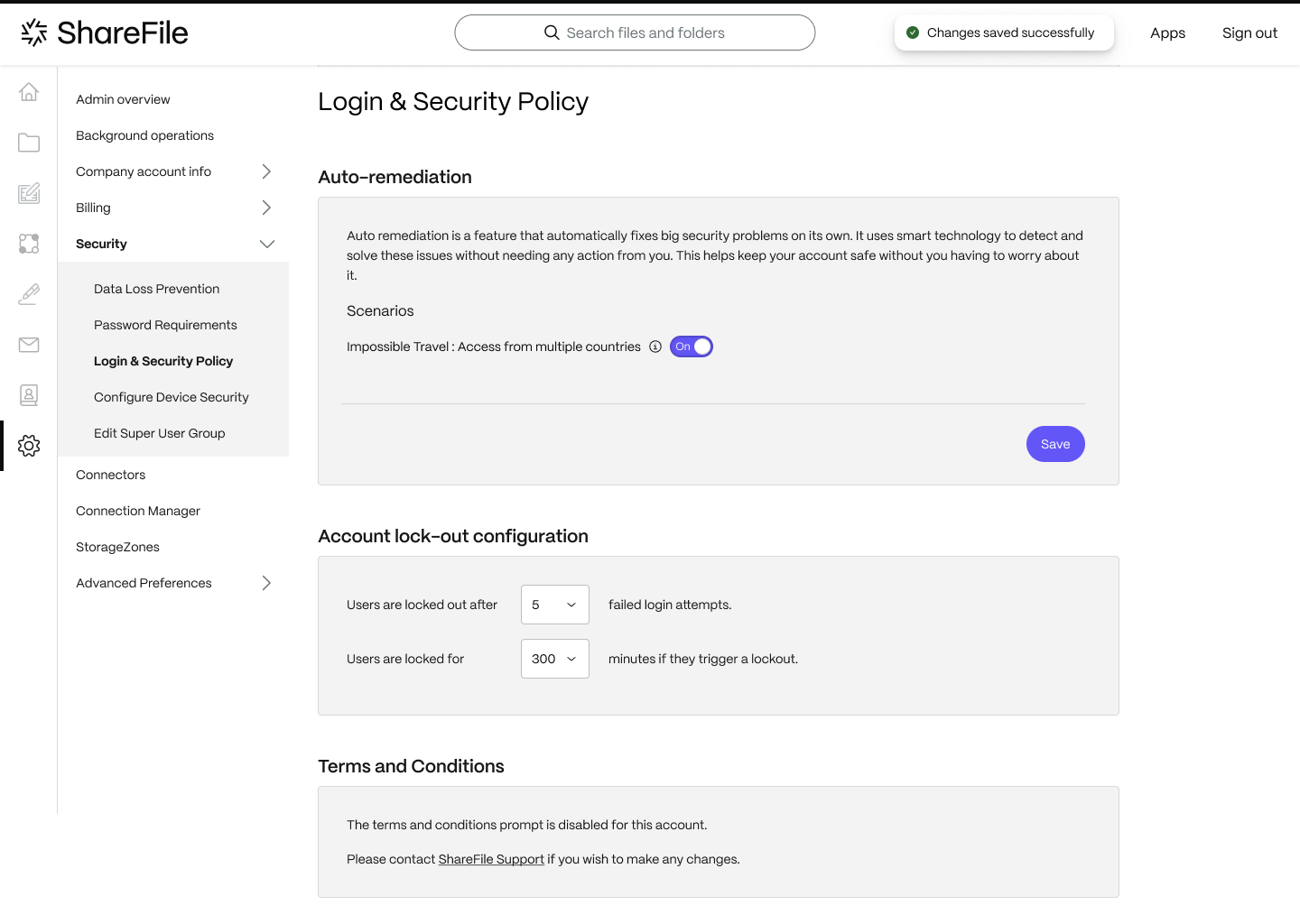
Frequently asked questions
What is the new ‘Opt-out’ feature?
The ‘Opt-out’ feature allows account administrators to disable specific auto-remediation scenarios within their security settings. This means that administrators can tailor the security measures better to fit the needs and preferences of their organization.
Who has the authority to use the ‘Opt-out’ feature?
Only account administrators, who are the owners of the accounts, have the authority to access and use the ‘Opt-out’ feature.
What happens if an administrator opts out of a scenario like ‘Impossible Travel’?
If an administrator chooses to opt out of an auto-remediation scenario such as ‘Impossible Travel,’ that scenario will no longer be active on their account. The specific security measure will not be applied unless the administrator decides to re-enable it in the future.
Can an administrator re-enable a scenario after opting out?
Yes, administrators can re-enable any opted-out scenario at any time. This flexibility allows them to adapt their security settings as their organizational needs evolve.
How can administrators access the ‘Opt-out’ feature?
A: Administrators can access the ‘Opt-out’ feature through their security settings. Detailed instructions on how to navigate and modify these settings are available in our user guide and support documentation.
Trend Change
A “trend change” refers to a significant shift in a user’s typical behavior pattern. This can be an indication of potential security issues or misuse of the account.
Examples of Trend Changes
- Accessing from Multiple IPs: Typically, a user accesses their account from a limited set of IP addresses. If a user suddenly starts accessing from many different IPs, it may indicate unusual behavior.
- Heavy Downloads: If a user usually downloads a moderate amount of data and then suddenly begins downloading large volumes, this could be suspicious.
Alert Mechanism
When such trend changes are detected, the system will automatically expire the user’s current password and mandate a reset for any subsequent logins. The user will then receive an alert email informing them of the unusual activity and asking them to change their password. This immediate action helps secure the account against potential threats.
Admin Control and Opt-out Option
Admin Control
Admins have the option to opt out of the trend change detection feature for their accounts. This means the trend change alerts and automatic password resets will not be applied to their users, allowing admins the flexibility to decide what’s best for their organization.
Alert Recipients
The alert is sent to both the account admin and the user. If there is a sudden spike in accessing from multiple IPs & heavy downloads, the admin receives an email notification with details about the activity and the username, while the user receives an email asking them to change their password.
Frequently asked questions
What should I do once I receive this alert?
Once you receive the alert, you need to change your account password immediately.
How can I opt out of this scenario?
Only account admins have the authority to opt out of this scenario. They can choose to disable the trend change detection feature for their organization.
Share
Share
In this article
- Understanding Automated Threat Remediation: Enhancing Security with Proactive Measures
- Actions taken on different scenarios
- Notification Process
- Frequently asked questions
- Threat detection & remediation visibility
- Opt-out from Automated Threat Remediation
- Frequently asked questions
- Trend Change
- Alert Mechanism
- Admin Control and Opt-out Option
- Frequently asked questions
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.