This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Single sign on (SAML)
Single sign-on (SSO) can be configured using various IdPs and certain SAML 2.0 or 3.0-based federation tools using basic, integrated, or forms authentication. This feature is available for:
- Standard
- Advanced
- Premium
- Industry Advantage
- Virtual Data Room
Notes:
- This setting requires all Employee ShareFile users to use their Active Directory (AD) credentials to login to ShareFile.
This setting cannot relate to Client users of the account.
- Admin employee users with “Configure single sign-on settings” permission can still login using their ShareFile credentials. This is for redundancy purposes in case there are any configuration issues with the identity provider.
Enforce single sign on
To enforce single sign on (SAML):
- From the ShareFile dashboard, navigate to Account settings > Security > Sign in policy > Single sign on (SAML).
-
Click Edit:
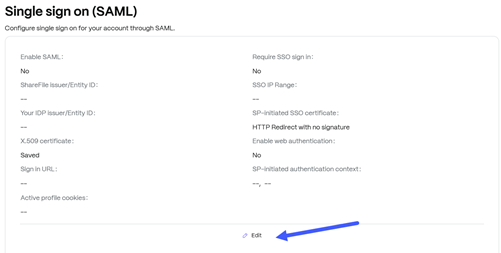
The Single sign on (SAML) drawer opens.
-
From the Single sign on (SAML) drawer, select Enable:
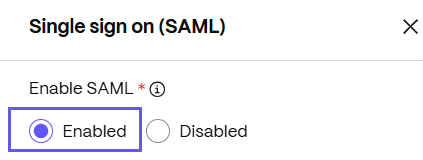
The single sign on configuration displays.
-
Specify the following information:
- ShareFile issuer/Entity ID - Enter the Issuer or Entity ID that represent the ShareFile service. This usually is in the form of a URL or a colon-delimited string.
- Your IDP issuer/Entity ID - Select the Issuer or Entity ID that represents your Identity Provider (IDP). Typically this can be left at the default setting.
- X.509 certificate - Enter the public portion of your X.509 certificate, including the—BEGIN CERTIFICATE— and —END CERTIFICATE— lines.
- Sign in URL - Enter the URL of your IdP’s assertion consumer service.
- Require SSO sign in - Require non-administrative Employees to log in using your identity provider.
-
SP - initiated SSO certificate - Sign SP-Initiated SAML Requests to your identity provider. Select “View” to retrieve the public certificate and add it to your IDP configuration. Choose from:
- HTTP Redirect with no signature
- HTTP Redirect (1024 bit certificate)
- HTTP Post (2048 bit certificate)
- Force SP-initiated SSO certificate to regenerate - Check this box to force ShareFile to regenerate the SP-Initiated certificate. Note that you will need to reconfigure your SSO service with the new certificate after saving.
- Enable web authentication - Select this check box if your account is using ShareFile Sync for Windows, ShareFile Sync for Mac, or the ShareFile Outlook Plugin and your SAML IDP is configured for web-based (Forms) authentication.
-
SP-initiated authentication context - Defines the method and comparison level for the authentication context. IDPs have to match the selected authentication method, when using the “Exact” comparison; or a higher relative strengh method when using the “Minimum” comparison setting. Select one of the folliwing options:
- Unspecified
- User name and password
- Password protected transport
- Transport layer security (TLS) client
- X.509 certificate
- Integrated Windows authentication
- Kerberos
- Active profile cookies - This is an advanced setting used by ShareFile Active clients - - i.e., Mobile clients, Sync engine, Outlook plug-in, etc. This parameter may be needed to automate selections in certain IDP configurations, such as Home Realm selection in Microsoft ADFS.
- Click Save.
Supported configurations
The following configurations have been tested and are supported for most environments.
More configurations
These configurations have been successfully configured and tested by our engineering teams. The following configuration documentation is subject to change due to continued product enhancements and improvements. The following configuration guides are presented as is:
Note:
ShareFile no longer supports custom logout URLs for the SAML configuration. All users will be directed to the ShareFile authentication service’s logout page when they sign out. Some of the above configuration guides may still provide a logout URL, but are no longer necessary.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.